The convergence of IT and OT (and incidentally industrial IoT) has been accelerated by digital transformation. European organizations are now facing difficult decisions when it comes to OT security environments, on both the technical side and on the people side when dealing with OT people who will have a very different vision of what security is or how it should be dealt with.
This was much discussed during IDC’s European CISO Summit last November as OT security is now top of mind for CISOs with OT operations in their organization as it expands risk in their environment.
The Challenge of IoT and OT for IT Security Teams
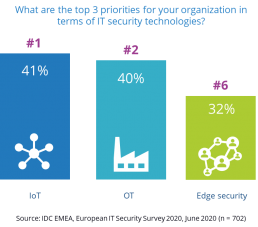
In June we conducted our annual European IT Security Survey of over 700 respondents in 15 countries. The data revealed that the top 2 priorities for security professionals in IT security technologies are IoT security (for 41% of respondents) and OT security (40%), with new concerns about edge security coming in sixth place for nearly a third of respondents (32%).
What Does Network Security Mean in an OT or Industrial IoT Environment?
Network security in OT environments means security products that can speak and understand the many proprietary industrial protocols, and provide both security operations center staff with increased visibility of the full operations and OT personnel with actionable information.
These types of security solutions are the ones gaining the most traction in Europe. They engage the existing customer base with the opportunity to modernize plant equipment with products that support remote monitoring, secure remote access, and data analysis to provide predictive maintenance, productivity improvements, and other long-term cost-effectiveness.
Network monitoring solutions can help maintain system resiliency in OT environments, which may be negatively impacted by the addition of wireless connectivity, sensors, and other supporting components.
In our annual European security survey, we saw how important IoT and OT security are for organizations in terms of:
- Safety and reliability of critical systems that operate 24 x 7 x 365 and involve processes with significant safety risks
- Industrial protocols, which are often unknown in the IT world and are inherently insecure
- Heterogeneous/legacy systems industrial networks, which include diverse assets and often consist of multiple connected architectures
- Volume of connected OT devices, which will continue to grow
What Can Security Vendors Do?
European organizations need some help developing an integrated approach to OT/IIoT security in three areas:
- People: Communication between IT and OT needs to be improved. Integration must appeal to both OT personnel, who need to understand the value of adding cybersecurity to their environment, and the security team, who need to mitigate risks to acceptable levels for the operations team.
- Technology: Organizations need to find the right security vendor that fits into the existing environment. Network security vendors must demonstrate how their network monitoring solutions can help maintain system resiliency in OT environments, which may be negatively impacted by the addition of wireless connectivity, sensors, and other supporting components.
- Support: Help with basic security hygiene and implemented best practices. This includes consulting and support services that help enterprises establish enforceable data governance, risk management, and compliance policies.

