Set 30 to 40 years from now, the 2014 blockbuster Interstellar tells the story of time travel, black holes and a rather clever farmer who runs a fully automated farm. In one scene he uses his laptop to hack an autonomous weather drone hovering over his fields. We don’t need to time travel, however, to see that autonomous farming or IoT drone hacking are already realities today.
Driven by improved productivity, cost optimisation and customer experience, the IoT industry has matured beyond Alexa, wearables and fridges that tell you when you’ve run out of milk. IoT covers critical infrastructure that keeps us safe during routine brain scans, regulates the moisture levels of tomatoes grown in greenhouses so that we can eat them in the middle of winter, and guides AVs driving through crop fields killing weeds.
IoT use cases bring a wide range of benefits — but can also lead to serious attacks with potentially fatal consequences.
It’s Relatively Easy to Hack IoT and Router Devices, Especially at Home
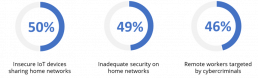
As remote work increases, senior IT executives worry about the number of insecure IoT devices shared at home, our inadequate home network security and the growing attacks on remote workers by cybercriminals (see Figure 1).
Figure 1
Q. What are the main concerns for your organisation around remote working and IT security?
When routers and IoT devices are poorly configured (no certificate = unencrypted), or if they suffer from systemic vulnerabilities, attacks can come from anywhere on the internet. According to the IoT Security Foundation, the most disturbing aspect of poor device configuration is just how widespread it is.
With weak password protection (if there is any at all), lack of regular patches and firmware updates, insecure interfaces, unencrypted traffic, poor IoT device management and the shadow IoT skills gap, it’s no surprise that even a half-decent hacker can hack IoT devices and expose the underlying network relatively easily. It might make you think twice about boarding a smart lift to the top floor.
IoT Adoption Outpaces Industry Standards
The European Telecommunications Standards Institute (ETSI) is addressing these vulnerabilities and is setting standards by:
- Discouraging IoT providers from selling IoT devices with universal default usernames and passwords
- Implementing a vulnerability disclosure policy to monitor, identify and rectify vulnerabilities through timely software updates
- Storing sensitive security parameters in persistent storage within the device
- Implementing updatable cryptography algorithms to communicate securely and protect personal data with in-traffic encryption
The reality is that standards have often lagged technological implementation. It will take some time for them to gain momentum while IoT innovation moves beyond the home and onto the factory floor.
IoT Zero Trust to the Rescue
With the perimeter blurring it’s no longer possible to secure everything with the current techniques, protocols and frameworks. Securing the devices is as important as securing the network used to communicate and ultimately transport your precious data.
Zero-trust architectures, based on the principle of denying access by default to anything inside your network, are becoming more important in the industry.
To the average user, zero trust looks like a set of annoying screens asking you several times a day to confirm if it is really you who is trying to access an application, often using a clever piece of software called two-factor authentication on your smartphone. Multifactor authentication is the price users must pay for the blurring of the perimeter.
But what happens when the users of the same network are not humans but IoT devices and industry robots? After all, IoT surveillance cameras, factory robots and weather drones don’t have smartphones. We might just be at the onset of multifactor authentication robot stress anxiety.
Fortunately for robots, a zero-trust security framework goes beyond multifactor authentication. Within the network realm, once IoT traffic is decoded (if OT) and the device has been identified, known vulnerabilities can be addressed. If there are no vulnerabilities the network performs behavioural analytics and assesses the risk and impact if assets have been compromised, and instantly deploys segmentation policies to devices belonging to similar processes.
IoT Zero Trust Is Not Yet a Top Customer Priority
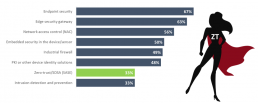
Endpoint security continues to be the main focus when securing IoT in the enterprise setting — the same type of security that is so open to attacks (see Figure 2).
Figure 2
Q. How does your organisation protect its IoT deployments?
With more workers planning to continue to work remotely post-pandemic, more enterprise applications moving into the cloud and more devices connecting to the network (IoT, OT), the value of wall-based security infrastructure diminishes.
Given their complex relationship, networking and networking security teams find it challenging to cope with low latency and bandwidth while securing users, devices and applications. This not only increases operational inefficiencies but also increases the risk of security breaches.
Extending a zero-trust architecture to IoT deployments requires a thorough understanding of all IoT systems on the network, not just traditional IT endpoints. This will enable IT teams to reduce the surface attack and risk without impacting availability, while also inadvertently bringing network and security teams together.
After all, the Interstellar hacks of the future are right here, right now …
For more information about IDC’s IoT and zero-trust research, industry trends, established and emerging use cases, and key players, please contact Romain Fouchereau, IDC European IoT Practice.