Building a 5G Marketing Proposition: Guidelines for Success
5G is being over-hyped. One routinely finds 5G described as “revolutionary” and “transformative” in its promised effect on people’s lives and on industrial processes. Meantime, early 5G adopters are discovering that the 5G services available now are essentially a faster version of 4G.
The “revolutionary” capabilities of 5G are still a year or two away. Some disappointment is already evident among early 5G adopters, and it is important to prevent this growing into a backlash.
The reality is that 5G is a complicated marketing proposition. Operators must simultaneously promote the real benefits that 5G can deliver today, and educate customers about what’s in the pipeline, without getting the two mixed up. The key to success is to develop a timeline-based approach to marketing 5G, with messages evolving as new technical capabilities such as ultra-low latency and network slicing come to market.
Such an approach requires a deep understanding of the applications that are enabled by each successive new 5G capability, and the business outcomes they deliver, coupled with a clear view of the timeline for the emergence of those capabilities.
What Are the Benefits of This Approach?
This approach to 5G marketing delivers two major benefits. Firstly, it anchors customers’ expectations to the reality of what 5G can do. Secondly, and more importantly, it enables operators to identify and go after low-hanging fruit: the 5G applications that can deliver substantial new value to their customers right now, because those applications rely only on faster data transmission.
In the healthcare sector, for example, major benefits can be delivered by enabling practitioners and paramedics to engage in real-time videoconferencing and to exchange high-resolution images over the mobile network. Healthcare organisations can derive another set of major benefits from examining and treating patients in their homes, instead of requiring them to visit a clinic or a hospital.
Remote biometrics, video consultations and even mobile clinics can all be supported solely by the high data-throughput rates of today’s 5G services.
easyJet Data Breach — Rebuilding Trust Now a Priority
If weathering the economic effects of the COVID-19 storm was not enough of a challenge, UK budget airline easyJet now must deal with the fallout of being victim to a major data breach. The email addresses and travel details of 9 million customers, as well as the credit card details of 2,208 customers, were exposed in a highly sophisticated cyberattack.
The data breach appears to be the latest in a series of attacks on airlines by suspected Chinese hackers, who target the bulk theft of travel records and other data.
easyJet first became aware of what was happening in late January, and took immediate steps to manage the incident, including notifying the UK’s National Cyber Security Centre (NCSC) and the Information Commissioner’s Office (ICO). In early April it informed those whose credit card details had been exposed.
The company claims there is no evidence that any of the personal information accessed has been misused. Because of the increased incidence of phishing attempts during the coronavirus outbreak, the company, on the advice of the ICO, is now taking steps to inform the rest of the 9 million passengers in case targeted.
Airlines and Data Breaches
When it comes to cybersecurity, the airline industry doesn’t have a great record, with several high-profile breaches in recent years. In 2018, Hong Kong’s Cathay Pacific Airways disclosed that hackers had accessed information on 9.4 million customers. Air Canada and Delta Airlines suffered similar data breaches.
The ICO announced last year that it intended to fine British Airways a record £183 million after a data breach exposed the booking details of 500,000 customers. Hackers had exfiltrated thousands of credit card numbers after installing skimming malware on its website.
Regulatory Steps
The data breach also raises the possibility of easyJet incurring a fine. The ICO sent out a clear message when it proposed record-setting penalties on BA and Marriot International: companies must ensure that their information security is in order and review and update this on a regular basis if they want to avoid significant penalties.
The ICO will be particularly keen to know whether easyJet had “appropriate technical and organisational measures to ensure a level of security appropriate to the risks.”
GDPR fines are, however, discretionary rather than mandatory, and where issued must be “effective, proportionate and dissuasive” for each individual case. The ongoing COVID-19 pandemic, however, adds a new dimension.
In recently issued guidance, the ICO said all enforcement actions will take into account “economic impact and affordability” and as a consequence it expects to issue lower fines.
Given the economic difficulties the airline industry now finds itself, there is probably little appetite for the ICO to impose a sizeable GDPR fine when the sector is already on its knees. A final fine against BA has still to be set, with the likelihood we will see a significant reduction from the headline figure in last year’s notice of intent.
Customer Trust
The extent of the damage from this data breach has yet to be seen, but it’s certain that customer and stakeholder confidence will be shaken as a result. easyJet may not have been obliged under the GDPR to notify customers whose basic booking details were compromised — only where the breach poses a “high risk to rights and freedoms” — but not having been transparent and honest earlier with customers could backfire.
Already facing customer anger over not obtaining refunds on their cancelled flights, sugar coating the breach may create more negativity and further diminish trust.
Rebuilding Trust After a Data Breach
Given the steady frequency of cyberattacks it is safe to say that data breaches are no longer a question of if, but when. A data breach will affect consumer trust and impact business reputation. The way in which organisations respond can go a long way to restoring that trust.
The faster the response, the greater the chances customers will react favourably. Keeping quiet about a data breach will only harm business reputation when the facts emerge.
Consumers are willing to forgive, but their trust can only be regained if organisations are responsive and transparent. This includes keeping customers informed about the steps taken to secure their data, as well as the preventative measures to ensure there are no repeats of the security breach.
Why the Edge Matters Before, During, and Post-COVID-19
Since the COVID-19 outbreak and subsequent lockdowns, we have seen that the majority of networks, including the internet, have been able to sustain the unprecedented growth in traffic volumes. There have been many efforts from communications service providers (CSPs), for example, to ramp up network capacity and connectivity, while video streaming providers have downgraded video to SD quality to decrease bandwidth needs.
Though all of these have had a positive impact on sustained connectivity, the resiliency of the networks lies largely in the deployment of content delivery networks (CDNs) or edge servers.
The Whole World Moved Online
COVID-19 has drastically impacted everyone and everywhere in the world, both in our private and work lives. The restrictions on movement and physical engagements have forced everyone to take our daily activities into the virtual space, affecting the way we communicate across learning, working, transacting, and consuming.
In addition to people having to work from home, academic lessons have been moved to the virtual space, doctors are consulting patients remotely, and people are shopping online more than ever before. Even social interactions such as meeting friends for drinks, partying, singing, and making music together have been moved online through video calling.
Streaming services have emerged as a leading source of entertainment and information, resulting in a surge in on-demand video services from the likes of Netflix and for gaming.
How do CDNs Work and What is Their Core Value?
The basic function of a CDN is to replicate or store (cache) the multiple copies of internet content. This includes web objects (text, graphics, and scripts), downloadable objects (media files, software, documents), applications (ecommerce, portals), live streaming media, on-demand streaming media, and social networks.
The main purposes of a CDN is to speed up the delivery of content to end users by minimizing latency, reducing bandwidth consumption and costs, and providing scalability needed to handle high peak traffic loads.
This all makes CDNs a requisite technology to battle the traffic surges that have taken place since the COVID-19 outbreak.
More Than Caching Alone
In addition to CDNs’ edge value proposition to bring content closer to users and regulate traffic in an efficient way, CDN providers, also referred to as edge cloud providers, also help (video) content providers and end users to minimize video traffic and download traffic.
From a video traffic angle this includes the optimization of bit rates during video traffic delivery. From a download traffic angle — software downloads, whether for video games, patches, or system updates, are among the biggest traffic drivers on the internet — CDN providers’ technology helps game publishers limit the speed of downloading and avoid congestion.
This is a powerful solution aside to shifting high-traffic download events to off-peak times to reduce spikes.
The edge is also important when it comes to security. Security at the edge increases endpoint and access security and limits hackers from accessing the corporate networks at its core.
The dramatic shift to home working in the past two months and the very short time span in which workplaces have been set up has considerably increased security risks for enterprises and fueled the need for edge security solutions.
The Surge in Traffic According to Global CDN Providers
Akamai, a key global edge cloud provider, witnessed a 30% increase (over March) in global traffic (and an increase of 20% in EMEA) delivered from the edge compared to the approximate 3% growth during a typical month. Peaks on Akamai’s platform caused by major streaming video events, including live sports as well as file delivery for software downloads and online gaming, have doubled in 12 months. Akamai reported peak traffic of over 165Tbps — more than double the peak of 1Q19.
Other key global players such as AWS Cloudfront, Verizon, CenturyLink, Limelight, and Microsoft Azure CDN also indicated large traffic volumes from their cloud edge/POPs. Verizon and CenturyLink reported an uptick in CDN traffic of 20% and 25% respectively. For Verizon, the majority of the increase came from VOD, dynamic, and static content traffic (entertainment, news, gaming, and content downloads).
For most CDN providers there has been a drop in traffic from live streaming events due to the cancellation of sports and entertainment events. Home schooling has fueled the uptake of traffic in the education sector and dependency on CDNs where online learning platforms in Europe connect millions of teachers and students every day.
Importance of CDNs Accelerates
Considering the massive uptake of CDN traffic volumes in terms of caching services but also related performance, (media) delivery optimization services, and CDN security services in the first quarter of 2020, IDC recently revised the CDN forecast upward. This resulted in an uplift of 6% for 2020 and 24% growth in 2020, compared with the previously projected growth of 16%. IDC expects the CDN services market in Europe to reach $2.6 billion in 2024.
It’s clear that CDNs have become more important in the past two decades as the world has shifted online, from shopping, to social networks, streaming media, gaming, and much more.
Needless to say, these CDNs and related edge cloud solutions have become even more important in the past three months to increase the resiliency of the internet as traffic volumes surged to new peaks. And this will continue as internet use grows further, even in the post-COVID-19 era.
To learn more, please contact Melissa Fremeijer or drop your details in the form on the top right.
A Hierarchy of Needs for Post-pandemic Planning
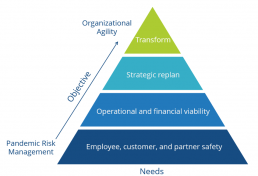
As your business picks itself up from the shock of the pandemic there are many methods you can use to start to plan your way through the short- medium- and long-term challenges ahead. My colleagues Tony Olvet and Megha Kumar from IDC Canada published an interesting approach recently which is based on the well-known psychological theory by Abraham Maslow – the hierarchy of needs.
In Maslow’s terms, this is a motivational theory where the needs at the bottom of the pyramid must be met before the one above becomes a motivator. This is a nice metaphor for business planning, in that we often find ourselves unable to “step back” and take a considered view of our surroundings while we are dealing with emergencies that require immediate attention.
I can hear lots of former colleagues in my head (especially CFOs!) shouting that the Operational and Financial viability should be at the bottom, since nobody can be made safe if the organisation isn’t functioning, and that’s a reasonable point of view. However I think we should approach this as we did the pandemic – we made things safe by switching to remote working and then we considered our sustainability, not the other way around.
Approaching safety from a technology mindset, the obvious thing is that we provide the remote working tools so that employees, customers and partners can stay in touch and keep those information flows in place. We also need to think about the way security is impacted by our changed circumstances so that we can safely manage our employees and clients personal data, for example.
Once we move on to managing the viability of our organisation, the most critical thing in my experience is good data. Measuring the things that matter in your business, from the use of your funding facilities, your sales pipeline, your conversion rates, your live orders, the time from order to invoice through to your ability to collect revenues are all absolutely vital to managing your way through uncertain economic times. Sometimes hard decisions are necessary but there is nothing worse than cutting the wrong place or cutting too deep – except perhaps not cutting enough resulting in the loss of everyone’s job. So those data and management information investments are worth their weight in gold as you go through this period, as are flexible and understanding technology partners.
If we can reassure ourselves that we have viability then we can face the future and understand the likely needs of our customers so that we can be sure that we have the right business model to operate successfully. Enhancing or rethinking our existing processes and technology solutions will be the key at this stage, as we focus on the value that we bring to the wider business ecosystem.
Only when we are comfortable that we have a safe business in all ways can we lift our heads to consider the future. This might happen quickly, it may take time, but being aware of where we are in this process is helpful. What happens to our business in a world where all our suppliers and customers have had to review all their processes, not to mention our employees? It would be optimistic in the extreme to think we carry on as before!
There are a thousand articles you can read about strategic planning and transformation, and IDC’s Digital Transformation Frameworks are available with case studies for just about every industry you can think of – so I won’t regurgitate them here, but of course I can help if you would like to know more. But to get there we need to be sure of our footing in the new economy and your choices around your technology investments will be more critical than ever, as we all attempt to prosper through efficiency rather than cutting to survive.
So in conclusion, if you’re not getting the reaction or engagement that you expect from colleagues as you look to the future and how you might transform your business or service, maybe their motivation is still in the lower sections of the pyramid and you need to help them through those as quickly as possible before they will join you in planning ahead.